In the previous post, we have discussed the trojan virus and also how to prevent this virus. In this article, we will discuss about ransomware that popular in this decade.
What is Ransomware?
Ransomware is a malware attack sent by hackers to lock and encrypt the victim’s computer. Then, the hacker will demand a ransom to restore access. More or less, that’s a simple description of what Ransomware is.
However, in reality how Ransomware works and the handling process is not simple. If you’re lucky, you can still regain access to your device. But if not, say goodbye to the important data you have.
If you don’t want this to happen, it’s a good idea to understand more deeply what Ransomware is and how to deal with it. This article is here to help you get the information you need about Ransomware.
Of all the types of malware that exist, Ransomware is one of the most dangerous. Unlike other malware, Ransomware can mess up a device’s system until it becomes inoperable.
Apart from that, Ransomware also has properties that can spread and infect nearby devices. So, it is very dangerous if not treated quickly.
Here are statistics on Ransomware developments in recent years based on the PurpleSec cyber security website:
- The average Ransomware ransom in 2021 increased by 82% year over year, to $570,000
- A total of 121 Ransomware attacks were reported in Q1 2021, a 64% year-over-year increase.
- Ransomware has proven to be on the rise with one type of Ransomware, Ryuk, which experienced a rapid increase of 543% during Q4 2018.
- In 2019, Phishing Ransomware increased by 109%, with new Ransomware variants growing by 46%.
- Ransomware attacks increased 41% in 2019 with 205,000 businesses losing access to their data.
- Ransomware has become a popular form of cyberattack in recent years, growing by 350% in 2018.
How Ransomware Works?
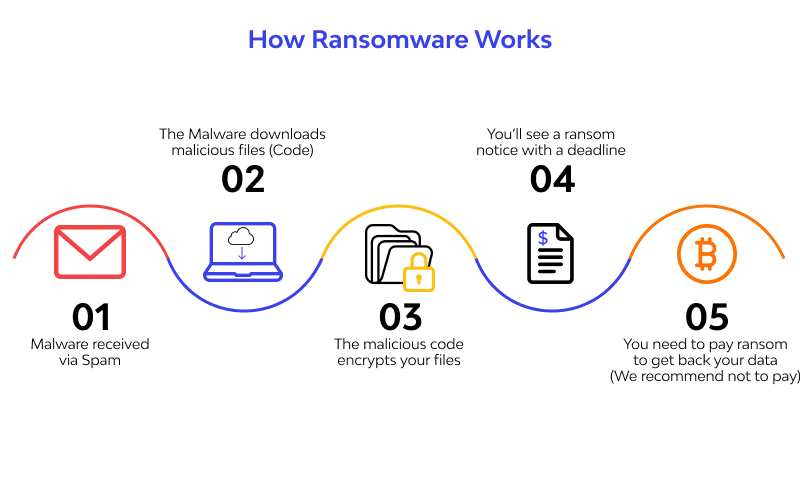
Generally, there are seven stages of how Ransomware works to disrupt the system on your device. Here’s the explanation:
1. Infection
The downloaded ransomware accidentally starts installing silently on your device.
2. Execution
Once installed, Ransomware starts scanning and mapping the location of files that will be the target. This malware can target files stored in local storage or cloud storage. In fact, several types of Ransomware can delete or encrypt backup files or folders.
3. Encryption
At this stage, the Ransomware starts working by conducting a key exchange with the Command and Control Server, using the encryption key to randomize all files found in the Execution stage. This type of malware also locks access to data on the device.
4. Notification
After successfully taking over the data on your device, Ransomware will usually pop up a user notification containing information on the ransom that must be paid to get the decryption code.
5. Cleaning
After successfully encrypting the desired data, Ransomware usually stops and deletes itself, leaving only the payment instructions file.
6. Payment
If you choose to pay the ransom, you will be asked to follow instructions. Hackers usually use hidden TOR services to communicate in order to avoid detection by monitoring network traffic.
7. Decryption
After making the payment, the victim will receive a decryption code to restore access to their device. Even so, paying the ransom is highly discouraged as there is no guarantee that your files or folders will return to how they were before.
Types of Ransomware
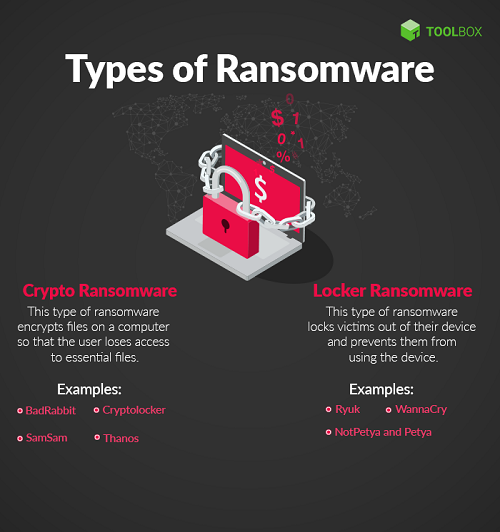
There are several types of Ransomware that are distinguished by how they work. Here are the two most common types of Ransomware:
1. Encrypting Ransomware
This type of ransomware infects devices by encrypting important files and folders on the victim’s device. After the target is successfully locked and encrypted, a notification will appear regarding the ransom that must be paid to reopen the locked data.
Example of Encrypting Ransomware:
- WannaCry
- CryptoWall
- CryptoLocker
- Locky
2. Locker Ransomware
This type of ransomware does not work by encrypting the victim’s files or folders, but instead locks the victim’s access to the device. Usually, the target of Locker Ransomware is file or device locking. But sometimes, this type of malware also targets the victim’s hardware such as a keyboard or mouse.
Locker Ransomware is a low-level annoyance that can be fixed by removing scripts, etc. Thus, the ransom paid for this type of malware is arguably less.
Examples of Locker Ransomware:
- Winlocker
- Reveton
How to Prevent Ransomware Attacks
Now that you know what Ransomware is, it’s time to learn how to prevent Ransomware to keep your device safe. Here’s what you can do:
1. Avoid web pages without HTTPS
HTTPS or Hypertext Transfer Protocol Secure functions to secure data exchange that occurs on the internet by encrypting data. HTTPS guarantees your security when visiting websites with HTTPS through 3 aspects: authentication, integrity and encryption. We have also written an article about how to setup HTTPS on your site.
Visiting websites that use HTTPS will help you avoid hidden malware attacks. You can find out if a website is already using HTTPS by checking the URL of the website.
2. Avoid files from unofficial sites
Just opening an unofficial site is dangerous enough, especially if you download and install something from that site. Files on unofficial sites are the most convenient places for ransomware to hide and wait for victims to download them.
Therefore, always try to download files from official sites that are guaranteed to be safe.
3. Avoid ads and suspicious links
Malvertising or malware advertising is a method that hackers often use to spread malware, including Ransomware. You can accidentally click on an advertising link, then without realizing Ransomware has been installed on your device. For this reason, be careful when you see suspicious advertisements or links on the internet.
4. Backup your data periodically
The way Ransomware works is by encrypting data and threatening to delete it if the victim doesn’t pay the ransom. However, if you have a good data backup, of course this won’t be a big problem. This is an important reason why you should always back up data regularly.
5. Install Antivirus and setup Firewall
Firewalls and antivirus are the most effective ways to prevent Ransomware attacks and other types of malware. Firewalls work by filtering what data is accessed by devices when connected to the internet.
The firewall will also act like a wall that protects the device from data theft by hackers. However, firewall protection alone is not enough, and hackers will always look for loopholes to get inside your device.
For that, you also have to install an antivirus to provide extra protection, especially from dangerous malware like Ransomware.
6. Use a secure network
For those of you who often use public WiFi, you have to be careful. Because not all public WiFi networks are equipped with security to encrypt the data you provide while surfing the internet.
As a result, your data can easily be leaked and known by hackers to deliver malware to your device. If you don’t want this to happen, make sure you always use a secure network.
Is Your Device Protected From Ransomware?
Getting hit by Ransomware attack and losing important data is the worst case scenario. For that, you need to really understand what Ransomware is and how to deal with it.
The most important way to prevent Ransomware is to increase awareness of the importance of device security. You can start by surfing the internet safely and not opening dangerous sites, and using a protected network.
Don’t forget to back up data regularly, activate firewalls as well as antivirus, and always update the devices you use. That way, the risk of your device being infected with Ransomware will be even smaller.
Also make sure you choose reputable hosting provider. To get complete protection on your website, you can also use ASPHostPortal hosting services. In one hosting service package you can get a free domain complete with SSL protection!

Yury Sobolev is Full Stack Software Developer by passion and profession working on Microsoft ASP.NET Core. Also he has hands-on experience on working with Angular, Backbone, React, ASP.NET Core Web API, Restful Web Services, WCF, SQL Server.